- +31 320 760020
- support@yokdata.com
Threat Intel firm Group-IB has released an analytical report on the previously unknown APT group RedCurl, which focuses on corporate espionage.
Group-IB, a global threat hunting and intelligence company headquartered in Singapore, has released an analytical report on the previously unknown APT group RedCurl, which focuses on corporate espionage. In less than three years, RedCurl attacked dozens of targets all over the world — from Russia to Canada. A presumably Russian-speaking group conducts thoroughly planned attacks on private companies across numerous industries using a unique toolset. The attackers seek to steal documents that contain commercial secrets and employee personal data. According to Group-IB experts, corporate espionage has so far been a rare phenomenon on the hacker scene, but the frequency of such attacks these days suggests that it is likely to become more widespread in the future. The group was first mentioned in Group-IB’s annual report “Hi-Tech Crime Trends 2019/2020.”
Group-IB’s new research contains the first ever description of RedCurl’s tactics, tools, and infrastructure. The report includes details about the group’s kill chain discovered by Group-IB’s DFIR specialists, as well as unique data that Group-IB collected during incident response operations related to campaigns attributed to RedCurl.
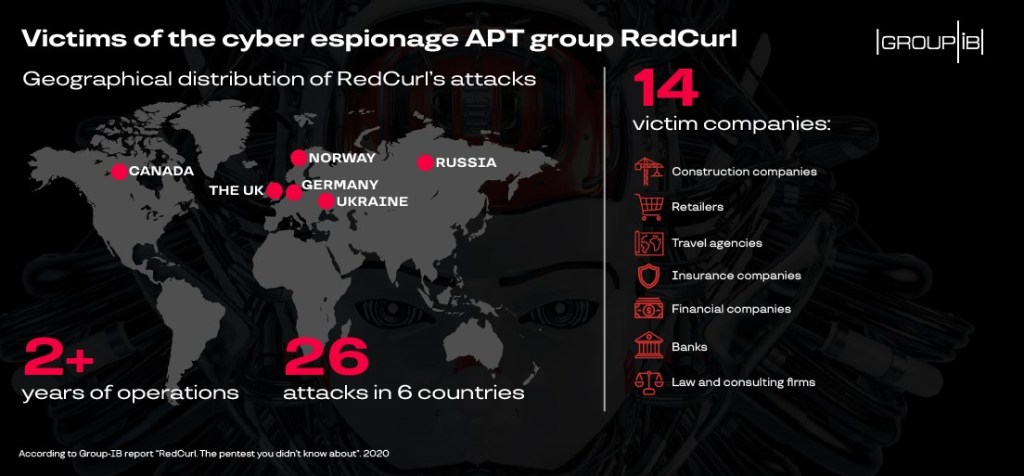
From Russia to Canada
The APT group RedCurl, discovered by Group-IB Threat Intelligence experts, has been active since at least 2018. Since then, it has conducted 26 targeted attacks on commercial organizations alone, including companies in the fields of construction, finance, consulting, retail, banking, insurance, law,and travel. RedCurl does not have a clear geographical link to any region; its victims are located in Russia, Ukraine, the United Kingdom, Germany, Canada, and Norway.
As part of its activities, the group acted as covertly as possible to minimize the risk of being discovered on the victim’s network. In all campaigns, RedCurl’s main goal was to steal confidential corporate documents such as contracts, financial documents, employee personal records, and records of legal actions and facility construction. This could indicate that RedCurl’s attacks might have been commissioned for the purpose of corporate espionage.
Full article on https://securityaffairs.co/wordpress/107094/apt/redcurl-hacking-group.html
#espionage #group-ib #redcurl #hack #threat